DMARC – vanliga fallgropar vid implementering
- Websecurity

Varför är DMARC viktigt och varför har många svårigheter att implementera det korrekt? Det anses idag som en hygienfaktor att skydda sig själv, men också sina kunder och leverantörer, från att ta emot mail som skickas ut i syfte att nätfiska. Genom att implementera DMARC sänker man risken markant för att ens domännamn felaktigt utnyttjas och används till just detta.
Det är inte tillräckligt med varken SPF, DKIM eller båda två för att skydda sig mot denna typ av bedrägerier. Det krävs också DMARC för ett fullgott skydd. Trots detta är det få som implementerat DMARC och många av de som försökt sig på att göra det har inte slagit på någon policy. Avsaknad av en policy gör skyddet helt verkningslöst och innebär att man fortsätter att utsätta sina mottagare för möjliga nätfiskeattacker. Det är inte speciellt förvånande att 91% av alla cyberattacker börjar med ett nätfiskemail.
“Given the information available on the risks associated with leaving your domain unprotected, it’s shocking the number of brands that still don’t understand the importance of DMARC,” sa Matthew Vernhout, Director of Privacy på 250ok.
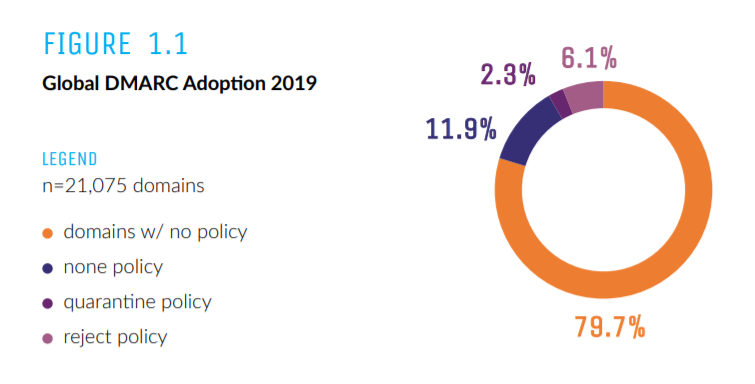
I 250ok’s Global DMARC Adoption 2019 rapport visar det sig att hela 79,7% av de analyserade domännamnen helt saknar en DMARC policy*. Det finns alltså inget giltigt publicerat DMARC record i DNS.
Att publicera DMARC records i DNS är ingen konst. Det komplexa börjar vid analysen av datan och vad man behöver göra med den information som genereras därifrån. Att så få bolag av de 500 största i USA ännu inte implementerat DMARC förklarar en stor del av denna komplexitet och presenteras också i 250ok’s rapport.
För mig som arbetar med detta dagligen så ser jag tre stora fallgropar:
Att anlita någon som har förståelse för hela processen är inte bara kostnadseffektivt utan också tidsbesparande. På Abion har vi paketerat tjänsten Email Compromise Protection (ECP) med alla delar du behöver för att säkra upp ditt e-postflöde på bästa sätt. Vi tar hand om hela processen inkluderat förstudie, implementation och monitorering, parallellt med täta avstämningar med dig som kund. Kontakta oss så berättar vi mer!
*250oks Global DMARC Adoption 2019-rapport analyserade domäner i en rad olika sektorer inklusive utbildning, e-handel, Fortune 500, USAs regering (verkställande, lagstiftande och rättsliga), China Hot 100, topp 100 advokatbyråerna, internationella ideella organisationer, SaaS 1000, finansiella tjänster och resesektorn. Rapporten kollar på om organisationen eller huvuddomänen, exklusive subdomäner, implementerat någon nivå av DMARC-policy från ”none” (bra), ”quarantine” (bättre), ”reject” (bäst) eller om de inte hade någon policy alls.